I basically put this whole thing out of my mind until a few days ago, out of the blue, they posted a message in the TG asking for people to test the updated app on Fuji.
They migrated to use ChainLink for this round. Which was a good idea for a general purpose app of this sort, but IMO not necessary for this kind of giveaway. The previous iteration was fine for this kind of giveaway (and I even suggested this to them when asked).
Testing, again
A two day notice is not a significant amount of time to do any kind of testing, we all have jobs and lives and shit. And I’m not sure how clearly it came across in the last post, but I was pretty annoyed at their team at this point.
So I honestly just clicked a few buttons, it worked, reported one minor UI issue, and gave it a thumbs up. I’m not going to do more than that for another $19 $COQ prize.
They posted the Solidity code in chat, but I glanced at it, saw how insane the logic was, said “I’m not getting paid for this shit” and moved on with my life.
For comparison, the last time I was doing this testing, I was examining HTTP responses, editing and sending custom curl requests, thinking about second order effects. For a key to open a box of garbage. What a fucking moron I was.
The sixth vulnerability
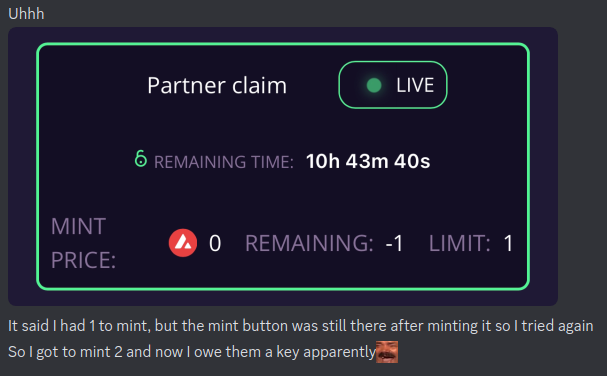
Then people started posting things like this.
Miph posted a really great explainer for this already:
This is bad, and an obvious thing to prevent. If you were REALLY attacking it, you could fit 500+ requests in and get 500+ keys.
If you’re not a developer, it’s hard to convey how embarrassing this kind of fuck up is. This is table-stakes stuff.
Things start going down hill
VQ doesn’t hold back on calling out bullshit, regardless of the consequences.
Prior to this, apparently Ferdy Frens did not get keys because of VQ’s history of tweeting, until it was clarified that he (like myself) aren’t on any NFT team and were just paid for the launch site and NFT generation.
After this tweet, apparently people started getting DMs from the Looty team like ‘did you give that fudder VQ a key’. Things escalate.
But back to the original problem
Lets just make up some bullshit to explain it!
The technical explanation is that they already give backdoor access to the boxes contract to burn the keys, making the approval here unnecessary and completely unrelated. And as you can see it triggers some very angry warnings. I assume that this was added due to some fundamental misunderstanding about how approvals work.
Things really escalate
And at this point, I start getting angry. Their team is very big on attacking and making false statements instead of listening and investigating and being accurate. I mentioned a few in the previous post, and above, but there have been others.
Everyone makes mistakes, and I’m pretty forgiving to people who admit them, less so when they try to bullshit their way out.
So I posted this ABSOLUTELY BLISTERING critique. Shamed them publicly.
They did not like that, and immediately posted in the group chat asking me what I meant. Unfortunately I didn’t take a screenshot of the result.
Vulnerability 7, 8, 9
I mentioned earlier that I wasn’t willing to audit this for free, because the code is so bad. And honestly, I still didn’t even try to figure out their minting logic. The code is very confusing. I speculate it doesn’t work properly.
But it’s very easy to spot the issue with minting multiple keys, blatantly obvious. I also quickly found that there were a few other additional problems with the keys code, including the unnecessary approval that Rabby flagged.
Moving on to the box opening code, and it seems there are a few serious vulnerabilities, and one issue they only dodged by virtue of using OpenZeppelin v5 instead of v4, which is not the kind of margin of error I think anyone should be relying on.
But surely, this is not the code they’re deploying right? No one would be so stupid as to leave this kind of gaping security hole in a production deployment, right?
Spoiler; bad things happen (in simulation, obviously I didn’t broadcast the tx).
Whitehackooooor (not me)
So, you might know the rest of this story, but for posterity.
The contract was already loaded with prizes at risk, that were just available for anyone who comes along to yoink, with no access controls.
Well, some of them anyway.
It seems like Looty was always destined for a Season 2 Part 2; they fucked up their code so badly that the best prizes weren’t even mintable. If you bought a diamond key for 30A or whatever, you had a pretty good chance of once again minting $19 of $COQ; technically, the prizes for silver keys were better than diamond due to how the logic worked out.
This is the funniest post Smitty has ever made. He peaked. It’s all downhill for him now.
The aftermath
Ultimately, all the prizes that were yoinked were returned to AvaLabs (who bought them in the first place).
I don’t think the Looty team will be paying a bounty for this. A generous third party provided a contribution.
Unsurprisingly, it seems like the box opening will be delayed.
The end?
Stay tuned for part 3, the boring part of the postmortem where we talk about what we learned and what we can do better next time.